3 Ways Historical WHOIS Records Can Give You Forensics Evidence
Ever heard it said that everything you put up on the Internet is there to stay? This post proves just how true that adage is. While many know what WHOIS records are, only a few m be aware that they can help keep tabs on all the updates and modifications made to a domain’s ownership record from conception to expiration.
Yes, every change in ownership that a domain name undergoes goes through can be kept in historical WHOIS records. And anyone who has access to a domain name history database is one step closer to uncovering everything there is to know about a particular domain’s owner.
Why would anyone want to dig up domain name history, though? Read on to find out.
What You Don’t Know Can Hurt Your Domain Reputation
No domain owner would ever want to land on anyone’s blocklist. Domain blocking can result in loss of customers, business opportunities, and, ultimately, revenue on the owner’s part. And it may be caused by:
1. Inappropriate Content
While we’re living in progressive times, many organizations still enforce strict limitations on the kinds of websites their employees are allowed to access on corporate-owned and network-connected systems. That’s not because they’re old-fashioned, it has more to do with productivity and cybersecurity.
Websites that fall under categories that include inappropriate content (adult, gambling, and the like), social media, video streaming, and online shopping are typically blocked from corporate networks unless, of course, they’re necessary for business operations. Not only does accessing these take employees away from doing their jobs, but some may be offensive to fellow workers and could land the organization in legal trouble. It doesn’t help that many network threats also come from these websites.
2. Ties to Malicious Activity
In most cases, access to domains deemed malicious on various malware and threat feeds and by cybersecurity solutions is also blocked. That’s pretty self-explanatory as no organization wants to become the next cyberattack victim.
Some of the threat feeds that you should never appear on include VirusTotal, Google Safe Browsing, and AbuseIPDB. All cybersecurity solution providers also maintain their respective blocklists that should be avoided at all cost.
3. Questionable Host
In some cases, landing on someone’s blocklist can be due to a more indirect cause—the domain happens to share an IP address or a nameserver with a malicious entity. That’s why it’s essential to know at all times who you’re sharing backend infrastructure components with.
Keeping tabs on your domain’s current state is important, but there are times when looking into its past may be necessary, especially if your present can’t tell you why you ended up on a blocklist. Digging deeper into domain name history may be the answer.
How Historical WHOIS Deep Dives Can Help
Companies that wish to avoid becoming part of any blocklist need to stay away from at least three telltale signs of nefariousness—malicious activity (phishing, spamming, malware distribution, and the like), organizations, and registrants (convicted felons or known cybercriminals). The good news is that doing that is possible throughout a domain’s life cycle via a domain name history checker. So, even if you’re using a recycled domain, you’re guaranteed to enjoy only the advantages and none of the disadvantages that an aged domain name brings.
Avoid Ties to Malicious Activity
Any domain that’s tagged “malicious” or “suspicious” in any threat feed is bound to get blocked. And these days, most if not all organizations are beefing up their cybersecurity posture by adding every indicator of compromise (IoC) to their blocklists. If you may think that ties to an attack from years ago can’t possibly hurt you, you’d better think again.
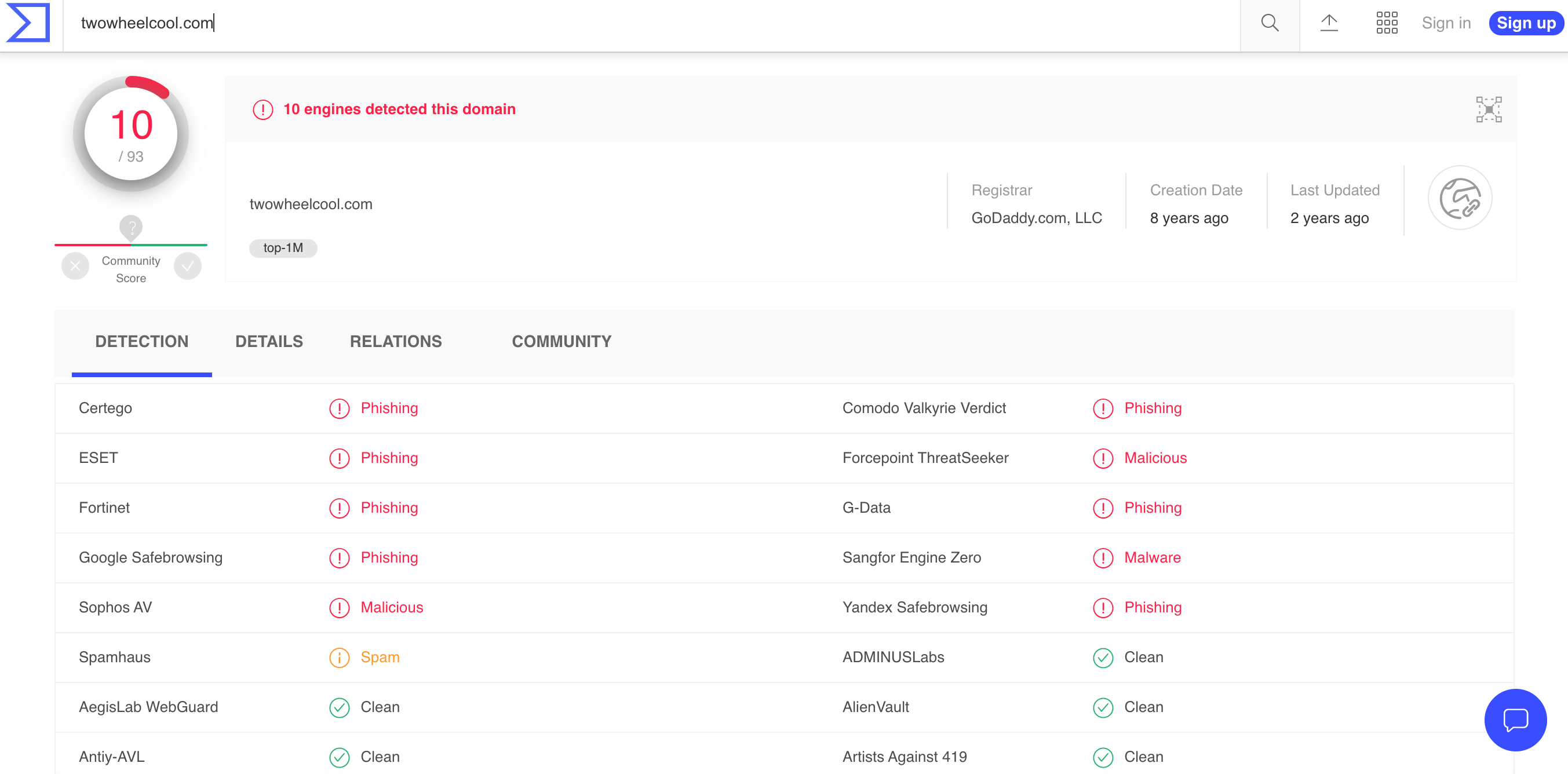
Let’s say that you’re looking to acquire the domain twowheel[.]com (it’s currently in use but for demonstration purposes, let’s pretend it’s available) for your up and coming business. Before taking the plunge and acquiring it, exert due diligence to make sure it won’t do more harm than good to your company. Subject it to a full historical WHOIS search.
Our domain name history query for twowheel[.]com revealed 24 historical WHOIS records, which isn’t surprising since it’s around eight years old. Here are a few other details we obtained:
- The domain changed registrars three times—GoDaddy (23 June 2012–1 June 2013), eNom (5 June 2013–2 June 2019), and NameSilo (30 September 2018–present).
- 79% of its WHOIS records contain publicly available ownership information. In particular, the domain’s registrant details were shown up until 4 May 2018. By 22 July 2018, its owner’s contact information had been redacted.
- Twowheel[.]com has undergone a total of 719 WHOIS record modifications.
- It has also changed ownership two times—B. Coleman (23 June 2012–2 June 2019) and an undisclosed registrant (22 July 2018–present).
A VirusTotal query for the domain showed that 10 antimalware engines detected it for phishing, spamming, and malware distribution as early as eight years ago and as recently as two years ago.
A subdomain of twowheel[.]com was also listed in PhishTank in November 2019.
While we can’t say that twowheel[.]com’s latest citations could be tied to its current owner; both fall within the period when the domain’s ownership record has been redacted. Regardless of which registrant is at fault, it may not be a good idea to purchase twowheel[.]com for business use since it is still on several blocklists.
Elude Connections to Questionable Organizations
These days, even cybercriminal enterprises mimic the structure of legitimate businesses. They maintain several domains and promote those to potential customers.
Just last month, the U.S. Department of Justice shut down an organization known as “Infraud Organization” after its leader pleaded guilty to conspiracy charges. Believed to have been operating since 2010, the cybercrime ring maintained the domain infraud[.]cc. It also owned the following domains, according to a report:
- infraud[.]su
- infraud[.]ru
- infraud[.]us
- infraud[.]org
- infraud[.]biz
- infraud[.]net
- infraud[.]info
- jabber[.]ms
Interestingly, Jabber is a Cisco trademarked brand that may confuse the application’s users should the domain figure be in a phishing attack.
Ties to Infraud Organization should be avoided at all costs, and one way to do that is by preventing any kind of connection to domains associated with Sergey Medvedev—its leader. To that end, using the domain contiguitycosmetics[.]com for your company is not a good idea. Why? Because a historical WHOIS query for it shows that it’s owned by a Sergey Medvedev since 29 November 2019. We can’t confirm that this is the same Sergey Medvedev, of course.
However, the “coincidence” (assuming it is one) should be checked. It’s customary for law enforcement agencies to investigate and take down all digital assets tied to proven criminal organizations and their members so the user of contiguitycosmetics[.]com may lose its domain or worse, be implicated as an accomplice.
Escape from the Shadows of Past Nefarious Registrants
Much like you’d want to avoid connections to shady organizations, you wouldn’t want to have ties to a wanted cybercriminal as well. If they’re charged and incarcerated, your domain may be taken down. That’s why it’s a good security practice to monitor law cybercriminal wanted lists. The Federal Bureau of Investigation (FBI) maintains one, and so does INTERPOL.
Supposing your domain coreltools[.]com got flagged for malicious activity and you are no longer able to receive emails from customers and other stakeholders. You’re not sure why and proceeded to investigate the matter. You found no issues with your current records, and everything is in order, but your domain remains inaccessible.
A domain name history query for coreltools[.]com shows that it was owned by an Ehsan Mohammadi based on its WHOIS record dated 7 December 2013.
A look at the FBI’s Most Wanted Cyber list includes a cybercriminal by the same name. Whether or not your domain’s past registrant and the wanted person are the same, it may be best to change business domains as that could be why yours is inaccessible.
—
Deep dives into a domain’s past can reveal how likely users today and the future are to trust it. Whatever your reason is for scrutinizing the integrity of a domain you’re interested in buying or investigating, using a domain name history checker is a worthy endeavor.
![A subdomain of twowheel[.]com was also listed in PhishTank in November 2019.](http://domains-index.com/wp-content/uploads/2020/08/VirusTotal.png)